
The digital world is entering a new frontier, where quantum computing challenges everything we thought we knew about cybersecurity. Quantum Key Distribution is rapidly emerging as the most promising defense against next-generation cyber threats. By leveraging the principles of quantum mechanics, QKD redefines secure communication, offering unparalleled levels of protection for critical data across industries.
Introduction to Quantum Key Distribution (QKD)
Quantum Key Distribution is a revolutionary method that enables two parties to exchange cryptographic keys with a level of security rooted in the laws of quantum physics. Unlike conventional encryption key exchange techniques, QKD makes any form of eavesdropping instantly detectable, ensuring that communications remain uncompromised.
With quantum computing poised to challenge classical encryption standards such as RSA and ECC, QKD emerges as a quantum-safe solution. Its ability to detect intrusion and prevent unauthorized access makes it particularly valuable for sectors where data confidentiality is paramount—like finance, healthcare, and government.
What Is Quantum Key Distribution (QKD)?
Quantum Key Distribution is a method of exchanging cryptographic keys between two parties using the laws of quantum physics. Unlike classical key exchange methods that are vulnerable to computational brute-force attacks, QKD ensures that any attempt to intercept the key will disturb its quantum state, thus revealing the presence of an eavesdropper immediately.
The most well-known QKD protocol, BB84, uses polarized photons to transmit each bit of the encryption key. The behavior of these quantum particles ensures tamper-evidence—a concept impossible in classical communications.
How Quantum Key Distribution Works
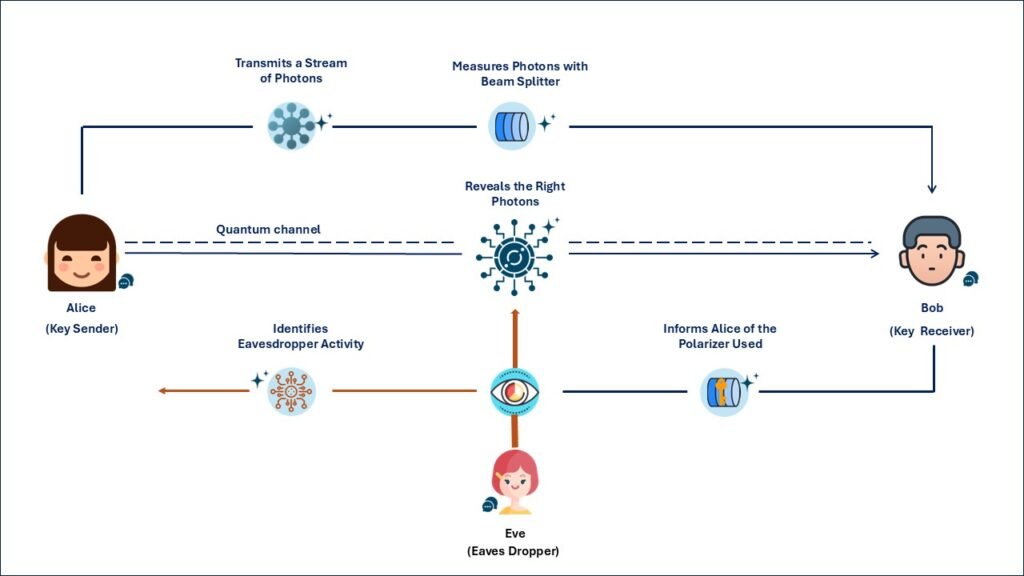
At its core, QKD involves:
- Photon Generation and Transmission: One party (usually referred to as Alice) sends photons encoded with key bits to another party (Bob) over a quantum channel.
- Quantum Measurement: Bob measures the photons in randomly chosen bases, and later communicates with Alice over a classical channel to compare a subset of their measurements.
- Eavesdropping Detection: If the quantum states differ from expected patterns, it’s a sign of interception.
- Key Sifting and Error Correction: Only matching measurements are kept, and any discrepancies are reconciled through error correction.
- Privacy Amplification: The final step compresses the shared information into a shorter, completely secret key.
This key is then used for symmetric encryption like AES, ensuring quantum-resilient secure communication.
Advantages of Quantum Key Distribution Over Traditional Encryption
1.Unconditional Security Based on Physics
Unlike conventional encryption, whose security depends on unproven assumptions about computational complexity, QKD is secured by the laws of quantum mechanics. No amount of computing power—quantum or classical—can break it without detection.
2.Real-Time Eavesdropping Detection
QKD does not just prevent interception; it actively detects intrusion attempts in real-time. Any measurement or observation of the quantum key alters its state and alerts both sender and receiver to a breach.
3.Long-Term Data Protection
Even if data is harvested today and quantum decryption tools are developed years later, data encrypted using QKD will remain secure. This is critical for sectors that must retain data integrity over decades, such as defense, healthcare, and finance.
4.Forward Secrecy
Every session in QKD uses a new key, generated dynamically. This ensures that even if a previous key were somehow compromised, it would not affect past or future communications.
Industries Adopting Quantum Key Distribution
Finance and Banking
Banks and financial institutions are increasingly exploring QKD to secure interbank transfers, payment systems, and blockchain-based platforms. Protecting financial transactions from quantum threats is vital for maintaining global economic stability.
Healthcare
Healthcare providers manage an enormous volume of highly sensitive personal data. QKD can ensure compliance with data protection laws like HIPAA and GDPR, while also safeguarding data from cyberattacks powered by quantum computing.
Government and Defense
QKD is being deployed to protect diplomatic communications, military command systems, and classified documents. Countries like China, the US, and members of the European Union are investing heavily in quantum communication networks.
Automotive and V2X Communications
With the rise of autonomous vehicles and vehicle-to-everything (V2X) networks, ensuring secure communication between vehicles and infrastructure is essential. QKD can enable quantum-safe OTA updates, protect vehicle firmware, and ensure tamper-proof transmission of sensor data.
Challenges in Implementing QKD
Despite its promise, QKD is not without obstacles:
- Distance Limitations: Optical fiber-based QKD systems are currently limited to about 100–150 kilometers due to signal loss.
- High Costs: Specialized equipment like single-photon detectors and quantum random number generators are still expensive.
- Infrastructure Compatibility: Integrating QKD with legacy network infrastructure can be complex and requires specialized expertise.
- Scalability: As of now, QKD is feasible mainly for point-to-point communication and not yet practical for global-scale networks.
However, solutions such as satellite-based QKD, quantum repeaters, and hybrid cryptographic models are quickly advancing to overcome these hurdles.
The Future of Quantum Key Distribution
Global momentum is building around quantum-safe infrastructure. The NIST Post-Quantum Cryptography Standardization Process is preparing guidelines for cryptographic algorithms resistant to quantum attacks. Simultaneously, QKD networks are being deployed in countries like China (Micius Satellite Project), Japan, Germany, and South Korea.
We anticipate a future where QKD works alongside post-quantum algorithms to deliver multi-layered, robust security. Companies must begin quantum risk assessments today to ensure they’re not left vulnerable tomorrow.
Integrating QKD into Your Cybersecurity Strategy
Organizations looking to adopt QKD should:
- Evaluate their most sensitive data assets and risk exposure.
- Invest in QKD hardware and software from certified vendors.
- Deploy pilot projects to test QKD with existing systems.
- Train cybersecurity teams on quantum communication protocols.
- Create a roadmap for phased adoption over the next 5–10 years.
The earlier the transition begins, the more seamless and cost-effective it will be when quantum computers become widespread.
Conclusion:
Embracing Quantum-Safe Communication with QKD
Quantum Key Distribution is not just a technological breakthrough—it is a strategic imperative for any organization committed to long-term data protection. In a world where quantum computing will eventually make today’s encryption obsolete, QKD provides the only proven method of ensuring that key exchanges remain impenetrable.
From banking and healthcare to national security and automotive, QKD is paving the way for a new standard of cybersecurity—one that is built not on mathematical guesswork, but on the certainties of quantum physics.


